Magento Security Alert: SessionReaper Vulnerability
A new unauthenticated RCE threat targeting Magento and Adobe Commerce
A severe Adobe Commerce vulnerability, identified as SessionReaper (CVE-2025-54236), is currently being exploited in the wild. This flaw can result in unauthenticated remote code execution (RCE) in Magento, meaning attackers can run code on a server without logging in.
If your store runs Magento 2 or Adobe Commerce, you must patch immediately. Unpatched sites are being targeted by automated attack campaigns that attempt to take full control of vulnerable servers.
Worried about SessionReaper?
Our experts can patch the SessionReaper vulnerability and perform a full security audit.
👉 Contact us today for expert help
What Is SessionReaper & How Can It Hack Your Magento Store?
SessionReaper (CVE-2025-54236) is a serious Magento security issue that can let hackers upload a fake session file and trick your site into running harmful code. In simple words: attackers can take control of your store without logging in — a classic Magento remote code execution exploit.
This Adobe Commerce vulnerability affects both Magento Open Source and Adobe Commerce stores. Adobe released an emergency Magento security patch in September 2025 to fix the issue. If you haven’t updated since then, your store may still be vulnerable.
How Serious Is the SessionReaper Threat?
According to Sansec Threat Intelligence, as of late October 2025, 62% of Magento stores remain vulnerable to a critical remote code execution (RCE) Magento attack with publicly available exploit details.
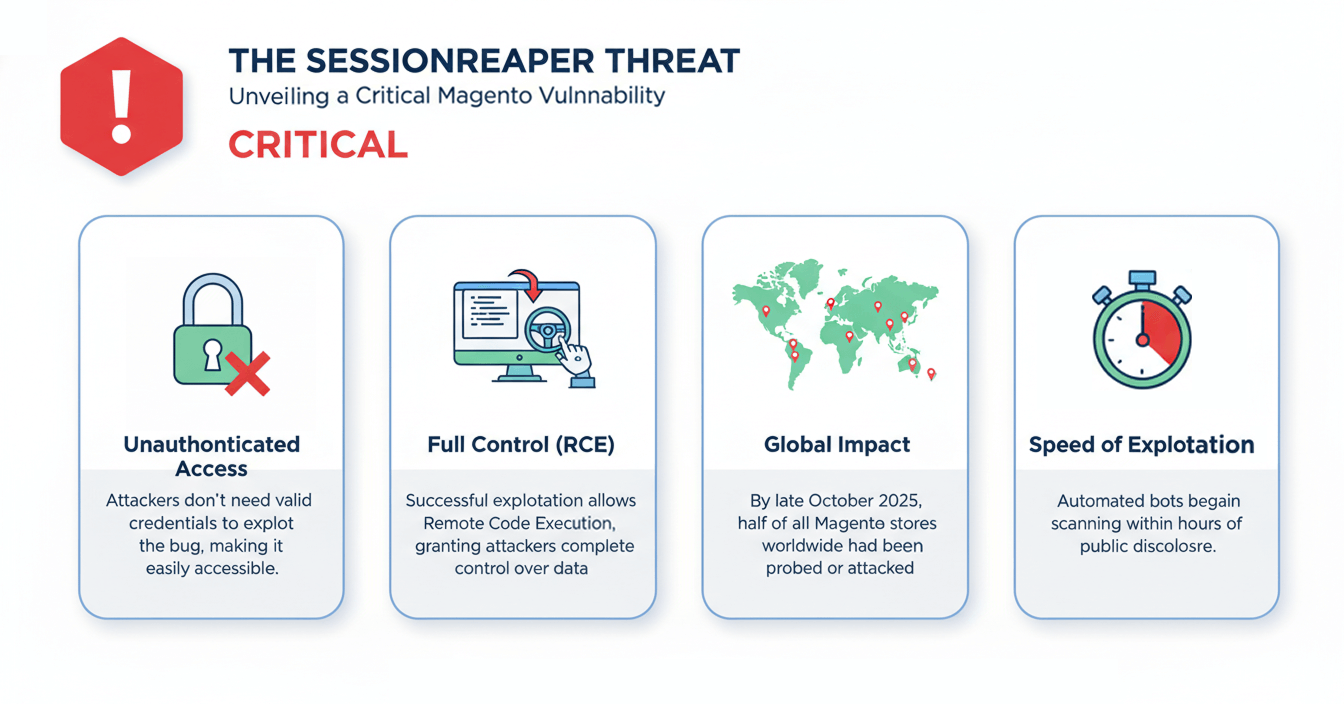
This vulnerability is especially severe due to several key factors:
- Unauthenticated access: Attackers don’t need valid credentials to exploit the bug.
- Full control: Successful exploitation allows Magento RCE, letting attackers modify data, install malware, or steal information.
- Global impact: By late October 2025, half of all Magento stores worldwide had been probed or attacked.
- Speed of exploitation: Automated bots began scanning stores within hours of public disclosure.
This is one of the most serious Magento security incidents in recent years, so quick action is essential.
Who’s Impacted by the SessionReaper Flaw?
The SessionReaper (CVE-2025-54236) flaw impacts both Adobe Commerce and Magento Open Source, including most releases issued before the September 2025 security update.
According to Adobe’s official guidance, this Adobe Commerce vulnerability affects:
- Adobe Commerce (all deployments) — versions earlier than 2.4.9 (alpha and beta builds included)
- Magento Open Source — versions earlier than 2.4.9
- Adobe Commerce B2B — versions earlier than 1.5.3
- Custom Attributes Serializable module — versions 0.1.0 through 0.3.0 should be updated to 0.4.0 or later
In simple terms: if your store has not been updated since September 2025, it’s vulnerable to an unauthenticated RCE attack that could allow full server control — a classic Magento RCE scenario.
Adobe’s patch closes the hole in the Commerce REST API, which attackers can abuse to upload malicious session files or take over customer accounts. Installing the latest security bundle (APSB25-94 or later) fully resolves the issue.
How to Fix the SessionReaper Vulnerability
To fix the the SessionReaper Vulnerability you need to:
- Install Adobe’s official patch right away. This closes the vulnerability that enables unauthenticated RCE.
- Enable or update your Web Application Firewall (WAF). Cloudflare, Fastly, or specialized Magento firewalls can block exploit traffic.
- Inspect upload folders. Check pub/media/customer_address/ and other writable directories for unknown files. Remove or quarantine anything suspicious.
- Run a malware and integrity scan. Look for new PHP files, unfamiliar code, or modified templates.
- Rotate admin passwords and cryptographic keys if you suspect compromise.
- Switch to Redis or database sessions instead of file-based sessions.
- Restrict file permissions. Only allow uploads where absolutely necessary.
These steps significantly reduce the risk of Magento RCE or further exploitation.
Need Help Securing Your Magento Store?
SessionReaper attacks are active now. Our certified Magento security team can:
- Apply the security patch
- Perform a full security audit
- Harden your store against future threats
Technical Details for Developers & Security Teams
- CVE: CVE-2025-54236 (CVSS 9.1 – critical)
- Patch references: Adobe advisories APSB25-88 and APSB25-94
- Risk factors: File-based PHP sessions + writable upload directories
- Mitigation steps:
- Apply the latest Adobe Commerce and Magento patches.
- Restrict write permissions in pub/media/*.
- Disable unused upload controllers.
- Add WAF or server rules to block serialized-object requests.
- Conduct integrity scans and rotate keys if compromise is detected.
Stay Protected
The SessionReaper Adobe Commerce, Magento vulnerability highlights how fast unauthenticated RCE attacks can spread once disclosed. Staying patched and following security best practices is the best defense.




